Compromise assessment service helps organizations evaluate if they have been compromised by advanced attack groups and if attackers are currently active in their environment.
Compromise Assessment is a unique service that allows organizations to evaluate their networks for the presence of advanced attack group activity. The Compromise Assessment has helped organizations identify and address issues that, in some cases, had existed for years and resulted in the theft of valuable intellectual property.
Designed to identify targeted attacks
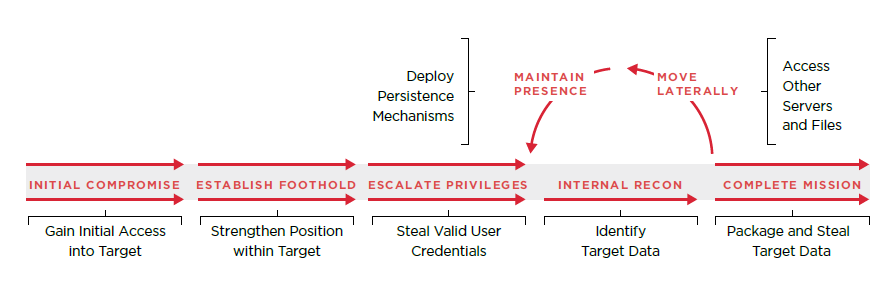
Over the past several years, advanced attack groups — often backed by organized crime syndicates and nation states — have targeted government and private sector organizations. These advanced attackers seek to remain undetected so that they can steal data over an extended period of time. They develop custom malware and use tactics that can often be difficult to detect using conventional approaches.
Evidence of attack groups
We work with Fireeye team, use experience gained over hundreds of investigations when assessing networks for the presence of various indicators of compromise including:
Re-used custom malware: Custom malware is often developed at great expense to the attack group. Consequently, they prefer to reuse it — or variants that have similar characteristics. Attack groups can oftentimes be discovered by identifying malware analyzed during prior investigations
Persistence mechanisms: A number of techniques can be used to establish persistence in a system. Windows registry entries can store malware execution parameters, malware can be placed in the Start Up folder and legitimate system binaries can be trojanized. Knowing what attack groups commonly do allows us to look for instances of those persistence mechanisms.
Lateral movement techniques: Most advanced attack groups obtain valid privileged credentials and use them to assess the environment. Knowing how they obtain those credentials and what tools they use to access other systems enables our expert to search for log and forensic evidence that is indicative of that attacker activity.
