
Over the past few years, Information Technology (IT) networks and Operational Technology (OT) environments have become interconnected, which has exposed a variety of vulnerabilities and weaknesses in the security of both, but especially OT. OT security and Industrial Control System Security (ICS), while improving, has not kept up with their evolving ecosystem, leaving systems exposed — as seen by attacks on Colonial Pipeline, the Florida Water system and other critical infrastructure. A recent Nozomi Networks-sponsored SANS 2021 OT/ICS Cybersecurity report reinforces this, revealing that ICS cybersecurity threats remain high and are only growing in severity.
While the results show a significant improvement from the last report published in 2019, 48% of respondents still admit to being unaware of whether their organization had suffered a compromise. This lack of visibility is a cause for concern, especially when visibility and detection solutions are readily available today to provide insights and awareness across an organization.
Most survey respondents rated the risk to their OT environment as critical, with ransomware and financially motivated cybercrime ranked as the top dangers. This is followed by nation-state attacks as well as unprotected and unmanaged devices. A concerning 15% admitted their organizations have experienced a breach in the last 12 months. What’s worse, for almost a fifth of these incidents, the initial infection vector came through the engineering workstation. Being such a critical piece of equipment, it’s a cause for concern that it was not only involved in the system breach but used as the source of access. In most cases, however, the dominant access vector was through external connection, with remote access services being identified as the most prevalent.
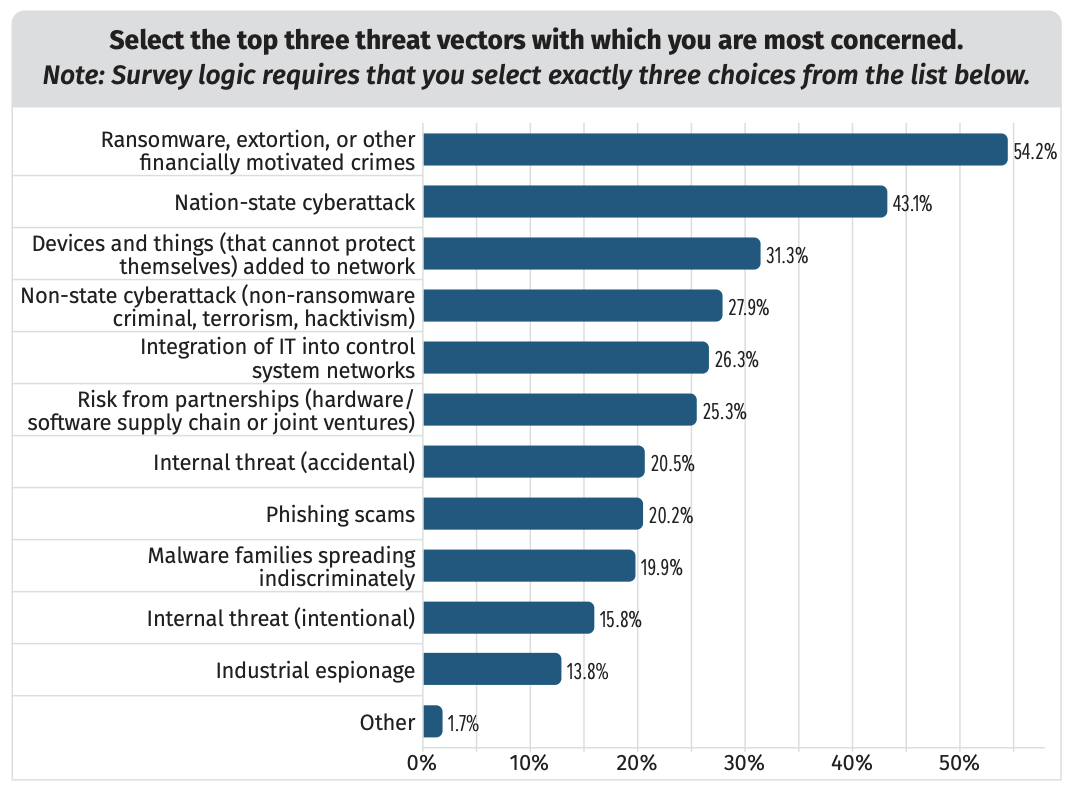
Image courtesy of Nozomi Networks
ICS Cybersecurity postures
For too long organizations have taken a wait and see approach to ICS cybersecurity, and the recent surge in attacks on these environments as well as critical infrastructure have sounded alarm bells.
Fortunately, this year’s survey found most organizations are finally taking the necessary steps to mature their security postures by improving their monitoring and threat intelligence capabilities. In fact, 47% of respondents say their organizations are increasing their security budgets and almost 70% of those involved in the study have monitoring programs in place for their OT environments. As a result, more than half can detect a compromise within the first 24 hours of an incident and can even move toward containment within 6-24 hours.
The survey found OT SOC adoption has increased by 11% since 2019. This is moving organizations away from traditional indicator-based Défense capabilities toward threat hunting and hypothesis-based security models. Consequently, IT teams no longer have to stretch their resources to cover both IT and OT security, leaving both more secure.
Cloud adoption in ICS
Surprisingly, there has been a notable increase in the use of cloud-native technologies in OT environments. Forty percent of those involved in the study revealed that their organizations are using some type of cloud-based service for their OT and ICS systems, with almost all of them using cloud technologies to directly support these specific operations.
Additionally, the majority of respondents are using cloud services for at least one type of cybersecurity function, including Network Operation Center (NOC)/SOC, business continuity and MSSP support. Most individuals surveyed believe their cloud assets are relatively secure, with less than a fifth classifying them as being vulnerable or at risk.
What do ICS operators need to focus on to protect themselves?
While the large majority of organizations have monitoring programs in place, the survey found they are still mostly looking at the IT aspects of their OT environments. They need to be correlating their IT and OT security telemetry as well as process data to truly understand potential impacts to safety and operations.
There’s also a need to focus on fundamentals. Too many respondents do not have a formal program for asset identification and inventory. Without this foundational step, further security investments may be invalid, misplaced, or over/under the actual needs.
Finally, ransomware is a huge risk, but it’s not one that is specifically targeting ICS. A malicious actor who is specifically targeting your ICS environment will usually not be as blunt or noisy as ransomware can be, but OT organizations are struggling to defend against ransomware. The impact of a ransomware breach still has potential to interrupt OT operations, even indirectly, so the risk should be tracked and mitigated.
https://www.securitymagazine.com/



